Complete Cybersecurity for SMEs
CYDEF has reinvented cybersecurity and made proactive threat hunting accessible to all.

CYDEF has reinvented cybersecurity and made proactive threat hunting accessible to all.


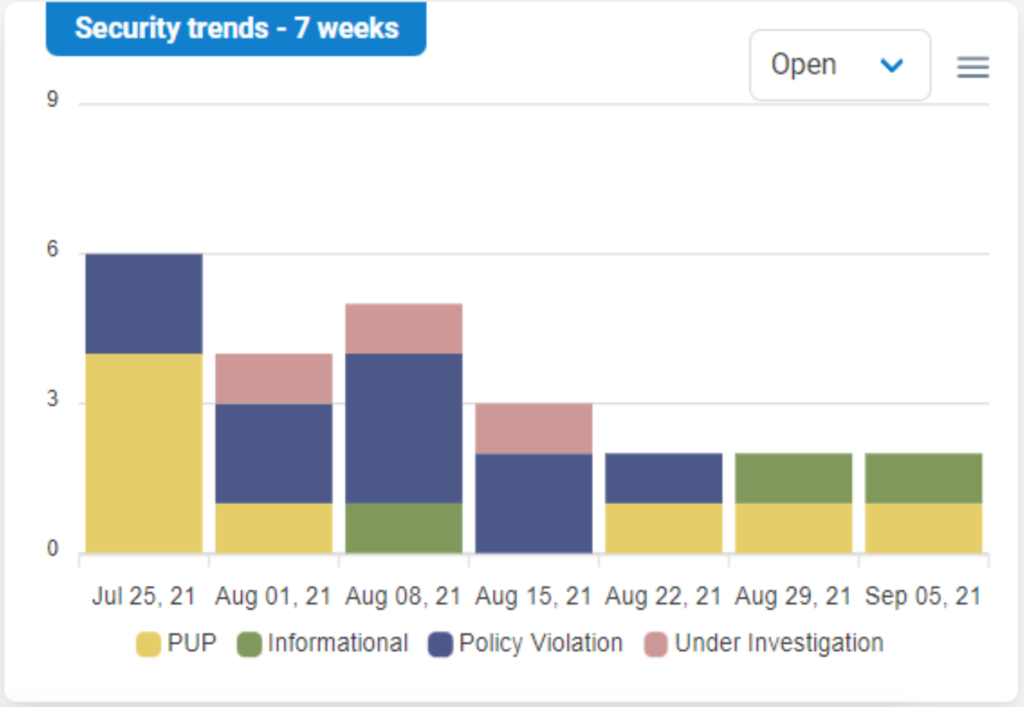
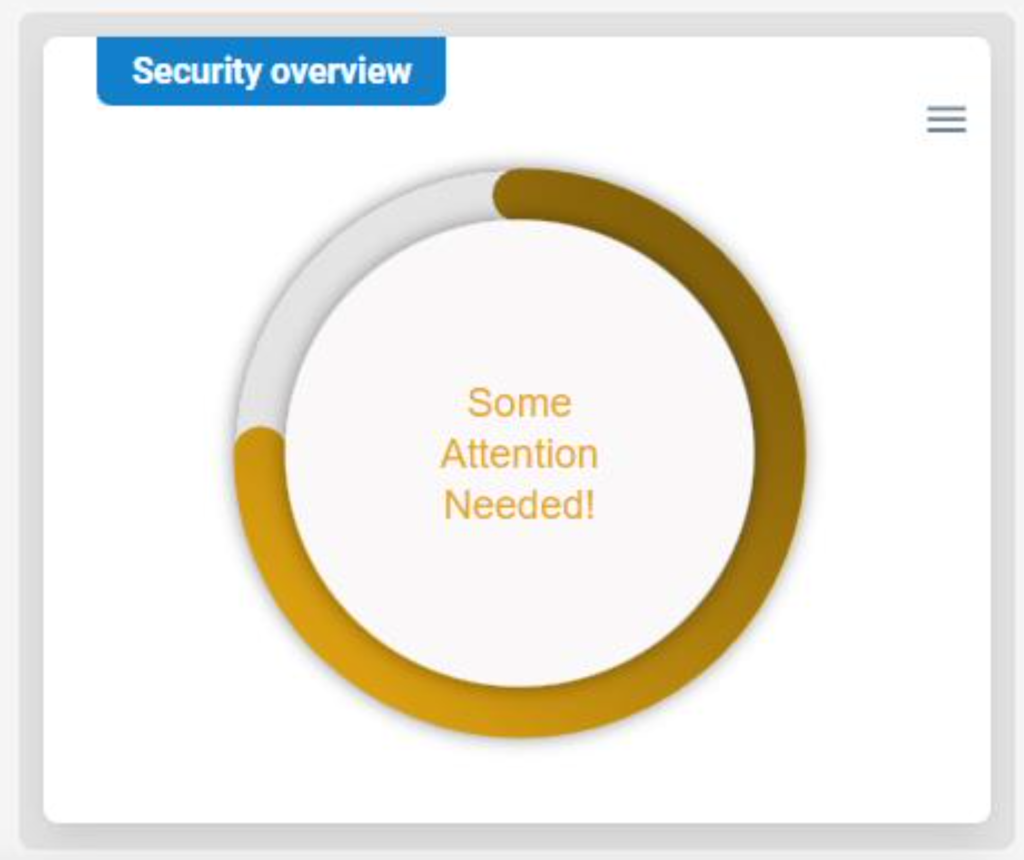
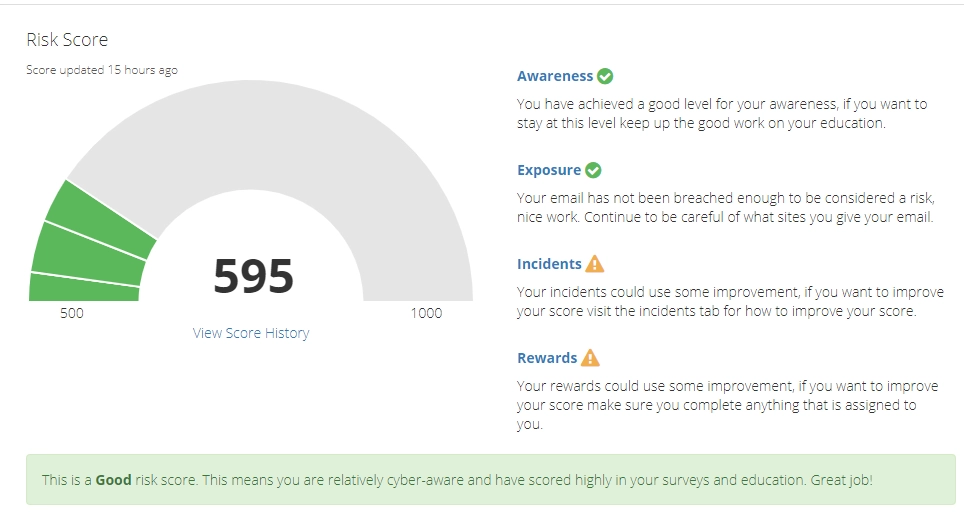
How are we different? Traditional cybersecurity analysis relies on alerts for “known bads” or suspicious activities. This means anything that isn’t alerted is implicitly trusted.
CYDEF follows a zero-trust model, CYDEF proactively and iteratively reviews the history of computer activity, regardless of whether it triggered alerts. This process is called “threat hunting.” it allows safe activities and investigates any anomalies that deviate from our baseline.
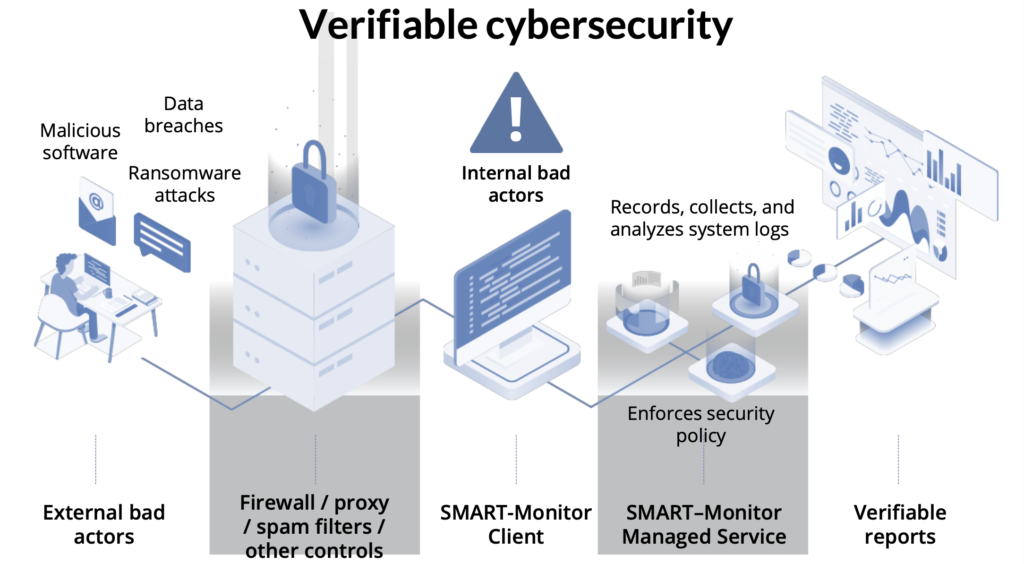
CYDEF list of safe activities grows exponentially with every device the tool protects, benefiting all CYDEF clients. This unique approach, combined with machine learning and human analysis, makes CYDEF solution revolutionary.
It gets better: You barely need to lift a finger. iValue & CYDEF provides people, processes, and technology as a turnkey service.
CYDEF’s cyber threat detection technology, provided as a managed service, gives you peace of mind. CYDED has the expertise to monitor your devices and operates the technology to ensure you’re always protected. CYDEF provides you with dashboards, reports, and tools to review the incidents. You also have access to the data CYDEF collects and our decisions. Why? First, it’s your data. Secondly, you can see how we work, understand what’s going on in your environment, and get recommendations to improve.
This text briefly introduces visitors to your main services.
A short description of the service and how the visitor will benefit from it.

A short description of the service and how the visitor will benefit from it.

A short description of the service and how the visitor will benefit from it.

A short description of the service and how the visitor will benefit from it.
304 million ransomware attacks occurred worldwide in 2020
40,000 brand new cyber attacks are invented every day
70% of attacks are targeted towards SMBs, due to lack of security
The average time to discover an attack is 207 days
Contact us today, and secure your IT environment from future cyber threats.
© 2024. All Rights Reserved. | Privacy Policy | Terms & Conditions | Developed By : Pixel Ideas Pvt. Ltd